“Hacking” someone’s social media account has been a concept for a long time, even back when Myspace and Friendster reigned supreme. This hasn’t changed one bit with modern social media such as Instagram, and if you’re reading this, you’re probably looking for a quick and dirty, automated way of getting into someone’s account.
Funny word, that, “hacking.” It comes with so much weight, evoking fanciful images of computer geniuses breaking into servers and stealing passwords.
In truth, however, outside of a few data breaches by actual evil geniuses, or critical programming bugs, very little hacking actually involves exploiting the social networks themselves. After all, these companies have spent hundreds of millions of dollars to ensure the security of account-holders’ data.
The reality is that there’s no real way to just drop someone’s Instagram handle into a box and magically get their password and other details. However, by taking advantage of your target’s gullibility or lack of personal security—rather than Instagram’s system integrity—you can get access to their account.
In this article, we take a look at effective ways to hack someone’s Instagram account, including some automated tools that can simplify the process.
1. Automated Tools
Getting Instagram account information is easy with automated tools. There are plenty of them out there that provide the functionality you need to hack into an account.
Some of these tools are positioned as child monitoring and safety software, but let’s be frank about things—they could just as easily be repurposed to perform spying duties, and get Instagram account information.
Many of these tools offer keylogging capabilities, which allows them to record all the keystrokes made on a device. If installed on a computer, for example, they’ll be able to read every single time that the keyboard was used, and what letters or numbers were pressed. If you sift through the logs, you may catch an Instagram password somewhere along the way.
Some tools actually have functionality specific to Instagram that allows them to directly read DMs and all links that are sent and received from a specific account. With such a feature, you won’t even need to hack into Instagram.
There are also tools that use brute-force methods to crack account passwords. These are the closest you’ll get to the actual hacking that is depicted in movies. Most of these basically try thousands of entries from lists of common passwords, and hope that one works. Others use more advanced techniques such as rainbow tables, which aim to reconstruct a password from encrypted hash data.
2. Reset Password
The simplest, non-automated way of attempting an Instagram hack is to use the “Forgot password?” feature that allows any user to change their account password if they’ve forgotten it.
Before you begin, you’ll need to already have access to one of three account access methods that your target uses. Either their email address, Facebook account, or phone will do.

Click on “Forgot password?” as indicated, then in the field that appears, enter your target’s username, phone number, or email address. Alternatively, click on “Log in with Facebook.”
If you used the target account’s username or email address, then you have to have access to their email account. Check their email for a message from [email protected], which includes a big blue button that links to a password reset page on Instagram. You’ll be asked to enter a new password from here.
If you used the target’s phone number, you’ll need to have access to their phone and the credentials needed to unlock it. You’ll receive an SMS from Instagram with a link to reset their password. Do the same as above.
Choosing to log in Facebook is fairly straightforward. You’ll be directed to the usual Facebook login screen. From here, input your target’s Facebook username and password, and you’ll have access to their account immediately.
This method is pretty much foolproof and will bypass two-factor authentication except in the case of Facebook login. However, it requires a lot of knowledge and access to the target in the first place. It’s definitely not ideal if you’re hacking someone you don’t know. It’s also not recommended if you’re part of a very small set of people with knowledge of or access to these accounts, because you immediately become a suspect.
3. Phishing (Creating Fake Instagram App)
You might have heard the term “phishing” in the past. It’s one of the principal ways by which malicious entities actually do get login credentials—not by fancy technological means, but by tricking people into revealing these details.
Phishing is the act of disguising fake emails, websites, and other communication channels as legitimate and official, then sending them to unsuspecting users to lure them into providing private information.
For example, a user who receives a fake email, ostensibly from Instagram, might be directed to a seemingly legitimate login link. They’ll input their username and password into the fields, and then rather than getting logged into Instagram, whatever they input will be sent straight to the hacker.
So how does phishing work for Instagram? How do you create the pages or emails necessary to trick users?
There’s a whole bunch of websites out there that make the process really easy for you. Most of them allow you to automatically create a website that looks exactly like the login screen of your chosen social media network. From there, you’ll be given a link that you can send to your target, which will entice them to enter their details.
To give an example, we’ll use one of the more effective sites out there, www.z-shadow.co. Start by heading to that site and creating an account. You may need to disable any ad-blocker software, as some of the site functions stop working if you’re running one.
From here, you’ll be faced with this screen:

Enter “Instagram” into the search box on the upper right, and you’ll find this:

Click on the “English” button, and a text box will pop up containing a link. Copy this link, or click the button on the right of the text box to copy it straight to the clipboard.
This is what that link looks like:
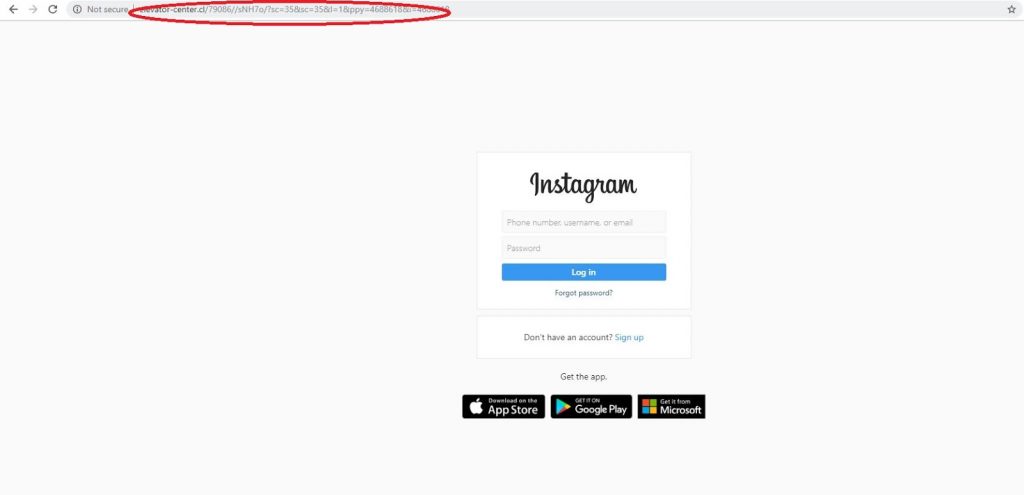
It looks exactly like the Instagram login page! Of course, if you look at the URL up top, it’s definitely not Instagram. However, most people fail to check their address bars before they input their personal information, so it’s still very possible for someone to fall for this trick.
The next step is to send that link to your target. Make sure to start a natural-sounding conversation and sneak the link in as though you’re showing them a picture from someone’s private profile. It should be something that won’t arouse suspicion when they’re met with an Instagram login screen. You can also reduce the chance of detection by using a URL shortener such as https://bitly.com/.
The minute they input their login information, they’ll be directed to a different page without being notified of anything wrong. However, their information will actually be recorded to your z-shadow.co account. In fact, if the z-shadow.co page is open when they input their information, you’ll get a notification, consisting of a bell sound, that tells you that you’ve got a hit.
To view the passwords that you’ve successfully phished, click on “My Victims” in the top menu bar.

You’ll be greeted with this list:
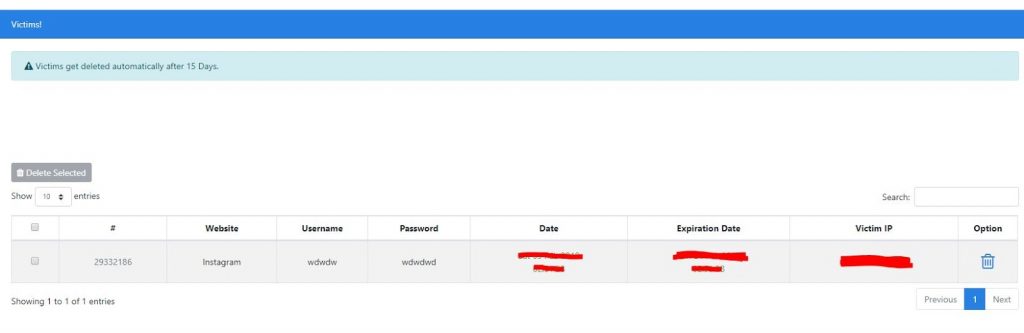
The username and password will be revealed in plaintext to you, along with the exact date and time that the information was inputted. You’ll also get the victim’s IP address for your reference.
Each of these entries will be deleted 15 days after they’re received, so make sure to save the information immediately, so that you don’t lose it.
The effectiveness of phishing is often dependent on the packaging, so to speak. You need to create a narrative that will make it reasonable for your victim to expect an Instagram login link. Once they’ve taken the bait, though, the accuracy of the Instagram phishing page’s appearance will definitely get them.
Keep in mind that this method will fail if your target is somewhat aware of security practices, and checks the URL before they input anything.
In addition, if your target uses two-factor authentication for their Instagram login, then the username and password will be useless on their own unless you have access to their phone.
4. Keylogging
Ah, the keylogger. One of the great fears of paranoid security geeks for so many years, the humble keylogger has gained almost mythical status in the public perception of hacking, even though it’s relatively difficult to deploy if you’re not a malware developer.
Keyloggers are little bits of software that constantly run in the background of a target computer or mobile device. They record, or log, every single button press that is performed while the keylogger is active. They may then record these presses locally to a file on the device, or send it to a server or the hacker’s computer.
We mentioned keylogging in some of the automated tools above, but here, we describe keyloggers as software solely designed to log keystrokes.
Most people encounter keyloggers in the wild through malware. The malware makes its way to a target computer via an email attachment or some other infection vector, then installs itself and starts sending information back to the creator.
Alternatively, many public computers which allow unsecured application installs could have keyloggers running in the background, installed by malicious individuals looking to harvest login information. This is one of the reasons why you should avoid entering your account details on public computers.
Using a keylogger is simple enough, though most of them are paid apps. For this method, you need to have access to the target’s device. Purchase any of the following tools:
You’ll get a secure download link to each of them after your purchase is complete. Use this link on your target’s device to download it there.
Launch the app and it will start running in the background, beginning its clandestine collection of data. You’ll be provided with detailed reports on every keystroke made. It might seem like a lot of information to sift through, since every text, web browsing search, and random button press will be recorded. However, more advanced keylogger software can mark certain events such as Instagram login sessions, and provide notifications accordingly.
Using a keylogger requires you to have access to a target’s phone, so it’s definitely tricky to pull off. In fact, if you already have critical access that allows you to handle their unlocked phone, you can already do a lot of things with their Instagram account, such as view their DMs.
The username and password you get from a keylogger won’t work if your target has two-factor authentication. However, if you have access to their unlocked phone, you can use their two-factor token to log in, after you acquire their login information.
Keyloggers are also not going to be particularly useful by themselves if the user already has their Instagram account signed in on their browser and app, since they’ll never need to enter their password.
5. Social Engineering Skills
We previously mentioned that “very little hacking actually involves exploiting the social networks themselves.” This is because the vast majority of hacking involves social engineering, or manipulating humans into sharing private information. If that sounds like our description of phishing, that’s because phishing is a subset of the greater whole of social engineering.
Social engineering can involve anything from calling a target and pretending to be someone from an authoritative body to ask for a username and password, to calling up customer service and providing just enough information to successfully pass as someone else, allowing a hacker to reset passwords or get more information.
Social engineering, therefore, isn’t a single method to acquire your target’s Instagram information, but a variety of social tools and manipulative techniques that you can use to get that information.
You can also use social engineering to enhance the effectiveness of other methods we’ve described. For example, with phishing, you can combine the phishing login page with a fake email for a job offer, which includes an (fake) “Instagram link” to a company Instagram.
It might even work, albeit with much lower success, with the “Forgot password” method. You could call or text your target and say that you accidentally sent your password reset link to them. Then, send the “Forgot password” request to your target’s phone, and ask them to forward the message to you. You’ll receive the link and you can use it to reset their password.
For keyloggers, you may want to manipulate your target into entering their Instagram password somewhere, because if they’re automatically logged in to everything, then the keylogger will never have an opportunity to see the password typed. Try sending them articles or fake chain letters about Instagram accounts being hacked and exposed, which will encourage them to enter and change their passwords. Your keylogger will be able to read the replacement password that they’ll use.
Social engineering pits your own manipulative skills against the gullibility and security readiness of your target. Sometimes, it’ll take a perfect storm of you being a genius, and them being a total idiot, to make it work.
Conclusion
Hacking Instagram accounts isn’t going to be easy. You’ll need a lot of access methods, techniques, patience, and a heaping serving of luck to get anywhere. It also depends on how “hard” your target is, how tech-savvy they are or how prone they are to manipulation.
One of the best ways to improve success is to combine several of these methods together, as no single method is foolproof. Combining the email access you get from an automated tool, with a “Forgot password?” request to your target’s email, can get you easy access to a password reset method. Using social engineering to get phone access and then tying two-factor authentication to a third-party account that belongs to you is another method.
Each of these methods has its own strengths and limitations, and you need to cover all your bases if you want to be effective. You also need to remember that if you’re trying to hack the Instagram account of someone you personally know, you are at risk of discovery and being exposed any time you slip up with these methods. If you send someone a fake link to an obvious phishing site, and they notice it, you’re going to be in trouble.
These methods are also very difficult to use with people you don’t know. In fact, the only way to get them to work is to use some long-term social engineering to gain their trust. At this point, you’re better off aiming to be a good friend and becoming close enough to actually ask for their login details.
And of course, it’s nearly impossible to perform these techniques on someone with whom you have no communication. The same goes for your own Instagram account if you’ve accidentally locked yourself out and are looking for a way to hack back into it.
But if you’re able to use these methods effectively, with all the conditions, access rights, and required information on hand, you’ll be able to take control of your target’s Instagram accounts without a hitch.
Once you’re in, it’s important to do your work without causing too much of a fuss. Don’t upload or delete photos or send messages to other people.
This doesn’t apply if you’re trying to take control, of course. If you plan on taking over your target’s account and keeping it out of your their hands, don’t forget to change the alternate email address, phone number, and Facebook account associated with it so that they won’t be able to reset everything back. Once you’ve done this, there’s almost nothing they can do to secure it again, short of contacting Instagram itself.
Congratulations, you’ve just learned five solid ways of hacking Instagram accounts, which are still viable in 2020. Stay out of trouble!
Tags
- instahack by computer
- how to complete offer in instahack org
- insta hack app
- hack insta follower apps
